Let’s take a step back and consider a straightforward scenario: that of an online e-commerce website. Before you can order something, you need to register with that website and provide some basic details—a sign-in name, an email, a password, and so on.
A typical website such as the one shown in the following diagram may simply store your details in a database and, at its simplest, this may just be a user record in a table:
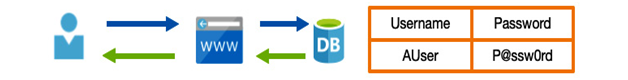
Figure 3.1 – Simple username and password authentication
For more advanced scenarios that may require different users to have different levels of access—for example, in the preceding e-commerce website—the user databases may need to accommodate administrative users as well as customers. Administrative users will want to log in and process orders and, of course, we need to ensure the end customers don’t get this level of access.
So, now, we must also record who has access to what, and ensure users are granted access accordingly, as in the example shown in the following diagram:
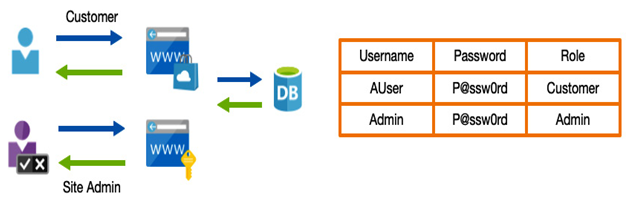
Figure 3.2 – Role-based authorization
The same would also be valid for a corporate user database. For example, the company you work for must provide access to various internal systems—payroll, marketing, sales, file shares, email, and so on. Each application will have its own set of security requirements, and users may need access across multiple systems.
For corporate users, Microsoft introduced Active Directory Domain Services (AD DS), which is a dedicated identity management system that allows businesses to manage user databases in a secure and well-organized way. Users in an AD are granted access to other systems (provided they support it) from a single user database. Microsoft AD DS takes care of the complexity and security of user management. See the example shown in the following diagram:
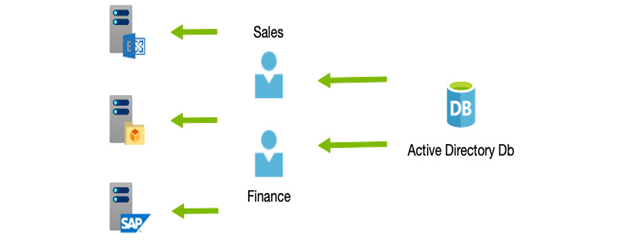
Figure 3.3 – AD
From a single account, IT administrators can provide access to file shares, email systems, and even web applications—provided those systems are integrated with AD. Typically, this would be achieved by domain-joining the device that hosts the application—be it an email server, web server, or file server; that is, the hosting device becomes part of the network, and AD manages not only the user accounts but the computer accounts as well.
In this way, the identity mechanism is a closed system—that is, only internal computers and users have access. Although external access mechanisms have been developed over time to provide remote access, these are still about securely connecting users by essentially extending that “internal” network.
Microsoft AD DS uses specific networking protocols to manage the security of devices and users—that is, the way devices communicate with each other—known as Integrated Windows Authentication (IWA); they are New Technology LAN Manager (NTLM) and Kerberos.
Microsoft AD DS is a common standard today for many organizations. Still, as discussed, it is built around the concept of a closed system—that is, the components are all tightly integrated by enforcing the requirement for them to be “joined.”